
Security and Compliance Built into Every Feature
Orange Logic’s digital asset management platform is engineered to deliver robust security and comprehensive compliance, offering peace of mind to industries that require rigorous standards:
- Industry-Recognized Certifications: Certified to meet stringent standards, including GDPR, HIPAA, and FINRA compliance, ensuring our solution aligns with critical legal and regulatory frameworks.
- Trusted Across Sectors: From finance to healthcare and beyond, leading organizations rely on Orange Logic for uncompromising security and dependability.
- Validated by Third-Party Experts: Regularly reviewed and validated by leading security organizations, including ISO 27001 certification, to maintain the highest levels of data protection and system integrity.
- Digital Rights Management (DRM): Advanced rights tracking to ensure compliance with licensing agreements, automated expiration controls to prevent unauthorized use, real-time monitoring of permissions, and dynamic watermarking with encryption to safeguard sensitive content.
Comprehensive Asset Security and Rights Compliance
Maintain control over your digital assets with innovative tools that safeguard data and ensure rights management compliance:
- Redundant Backup Systems: Ensure uninterrupted access with multi-server backups and failover mechanisms that protect against data loss.
- Intelligent Watermarking: Embed tamper-proof identifiers into assets for traceability and to deter unauthorized usage.
- Robust Digital Rights Management: Manage access with precision, leveraging auditing tools to monitor and enforce usage policies and rights.
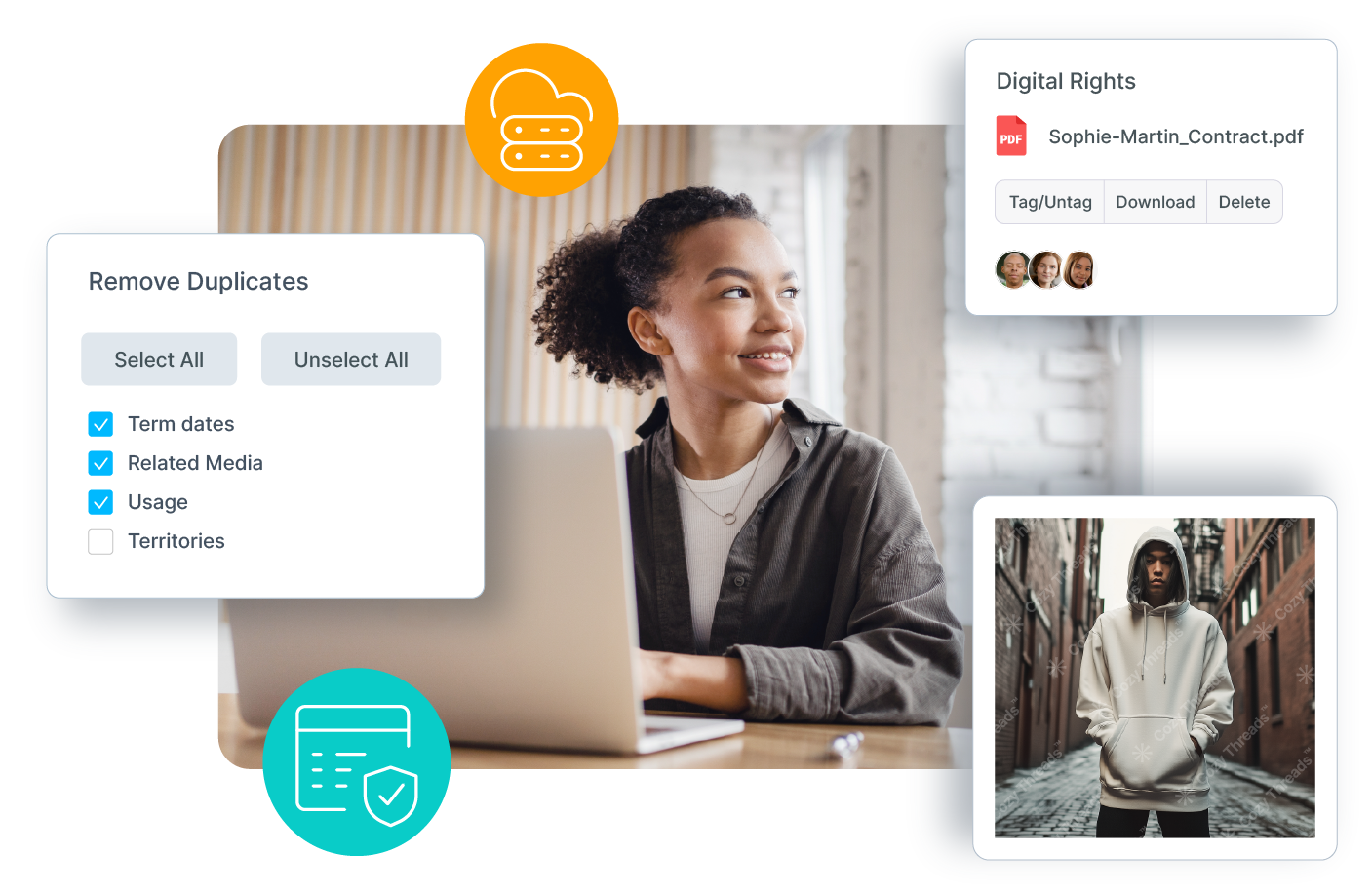
Tools Designed to Protect Assets and Maintain Compliance
Secure sensitive information and IP, while aligning with regulatory requirements using advanced DAM features:
- WORM Storage: Archive files with Write Once Read Many (WORM) technology to preserve data integrity and meet strict regulations.
- Compliance-Focused Templates: Streamline workflows with pre-built templates tailored for GDPR, HIPAA, FINRA and other industry-specific compliance requirements. These templates standardize processes across marketing, legal, and operational teams, simplifying approvals and ensuring alignment with key guidelines.
- Secure Sharing Portals: Facilitate secure sharing of assets with partners, vendors, and external stakeholders. Role-based access controls ensure that users only see the materials they are authorized to access. Detailed audit trails provide transparency and accountability, allowing you to track and validate external interactions with your digital assets.
- Enhanced Login Security: Enhance security by integrating Single Sign-On (SSO) for streamlined authentication. Support for multi-factor authentication adds an extra layer of protection, ensuring robust access control.
Empower Your Tech Stack with Proven, Flexible Solutions
Adapt your infrastructure to meet both operational goals and compliance requirements with versatile deployment options:
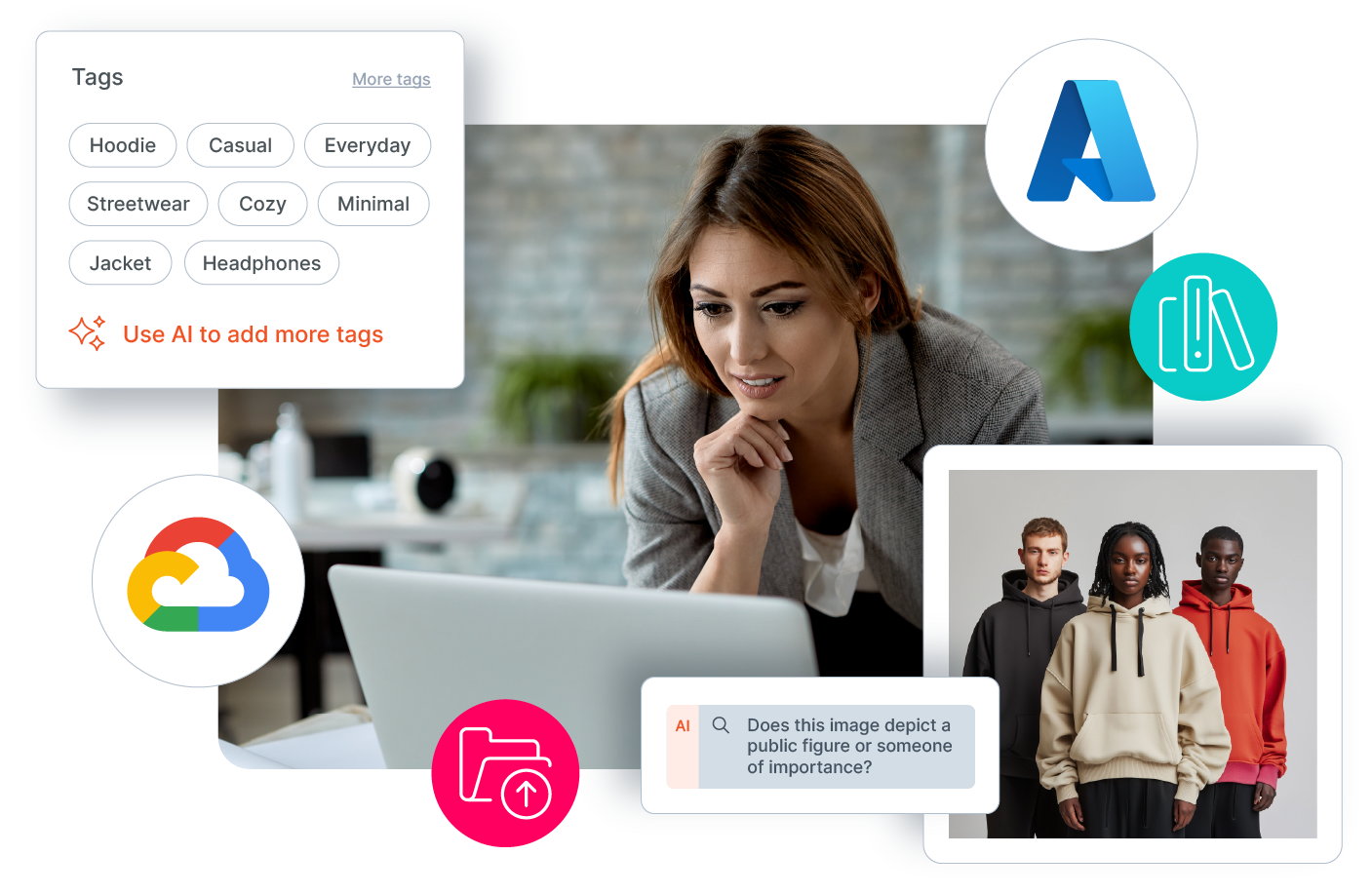
- Flexible Storage Options: Implement storage solutions that align with your operational and regulatory needs. Choose from industry-leading cloud services like AWS, Azure, or Google Cloud, hybrid setups, or for organizations with existing trusted infrastructure, bring your own storage (BYO).
- AI Tool Integration: Utilize cutting-edge AI tools out of the box to enhance operations, from analytics to automation, or integrate your own trusted AI models to maintain control and compliance. Deploy locally for sensitive data handling or seamlessly integrate with cloud-based AI platforms for scalability.
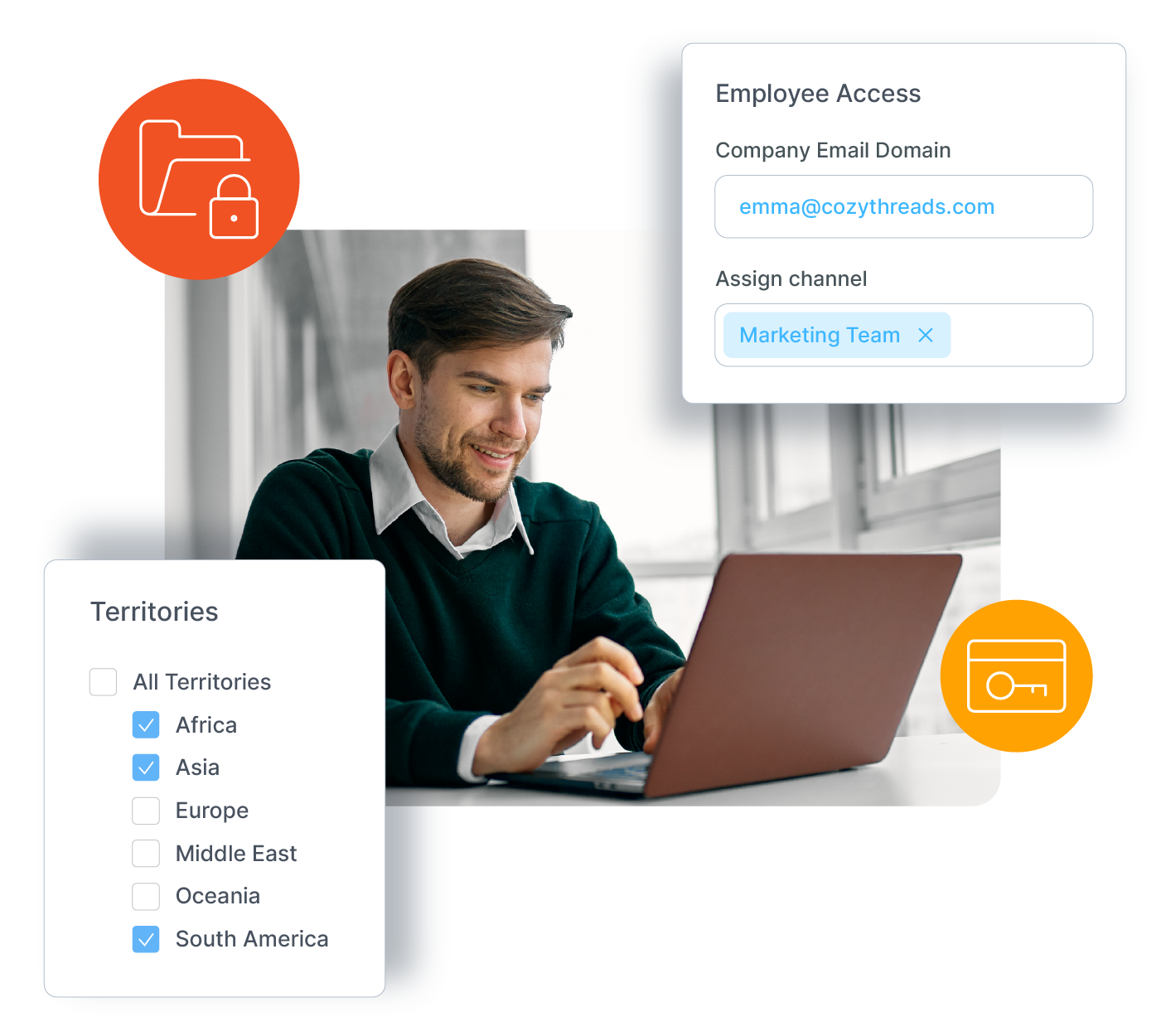
Advanced Permissions for Tailored Security
Control access and maintain compliance with detailed permissions tailored to your organization’s needs with Orange Logic's DAM platform:
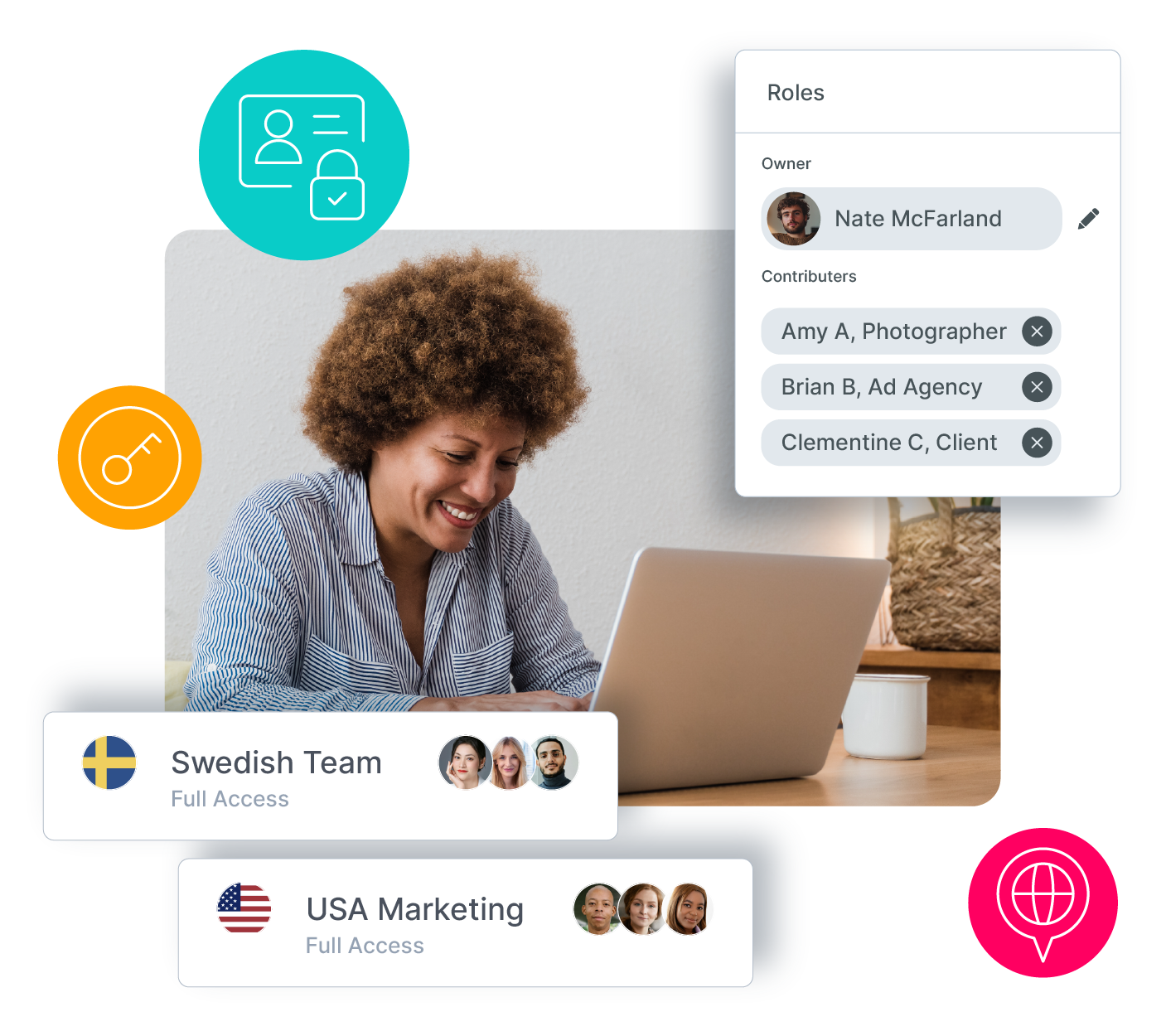
- Granular Role Management: Assign access rights based on roles, groups, or individual assets, with easy updates and validation.
- Dynamic and Location-Based Controls: Enforce data governance with geographic restrictions and adaptive permissions for cross-border operations.
- Rights-Specific Asset Management: Automate restrictions for expired or embargoed content and integrate licensing details directly into asset records.
- Secure Collaboration Tools: Facilitate external partnerships with controlled access while monitoring activity through detailed reports and notifications.
Reporting for Intelligent Insights & Audits
Harness the power of advanced reporting to optimize asset management, ensure compliance, and drive data-driven decisions:
- Data-Driven Insights: Understand how assets are being used, by whom, and in which contexts to inform future strategy and allocation.
- Audit-Ready Trails: Maintain detailed, real-time logs of asset interactions to streamline audits and support compliance across industries.
- Workflow Optimization: Use reporting to identify bottlenecks and inefficiencies, enabling smoother, faster operations.
- Compliance Assurance: Track regulatory adherence with metadata-tagged assets and automated compliance workflows.
- Strategic Forecasting: Leverage usage trends and performance metrics to forecast asset needs, allocate budgets effectively, and align with business objectives.
We're passionate about Security and Compliance
Orange Logic takes threats to the availability, integrity, and confidentiality of our customers’ digital asset management information seriously. We can give you peace of mind, knowing your assets are secure while being in compliance with your industries regulations.
Depend on the safest DAM software on the market
Safeguarding your assets is our top priority. We regularly run third-party checks of our digital asset management security system, in addition to our own security testing.
If you want to run your own penetration testing, you can do that, too. You can trust us to keep your assets safe.
Protect your assets with multiple backups
We keep multiple backup servers, just in case. If there’s a problem with the primary server, we’ll switch over to a backup server immediately. Your assets will stay secure, and you won’t experience any downtime from your digital asset management security system.
Security and DAM: Interview with Orange Logic’s Compliance Manager
We interviewed Briana Attinger, Compliance Manager at Orange Logic to learn how they secure customers’ digital assets and how they take take threats to the availability, integrity, and confidentiality of their customers’ information seriously.









